ZEBRA: Anonymous Credentials with Practical On-chain Verification and Applications to KYC in DeFi
| Abstract | ZEBRA is an Anonymous Credential (AC) scheme, supporting auditability and revocation, that provides practical on-chain verification for the first time. It realizes efficient access control on permissionless blockchains while achieving both privacy and accountability. In all prior solutions, users either pay exorbitant fees or lose privacy since authorities granting access can map users to their wallets. Hence, ZEBRA is the first to enable DeFi platforms to remain compliant with imminent regulations without compromising user privacy. We evaluate ZEBRA and show that it reduces the gas cost incurred on the Ethereum Virtual Machine (EVM) by 11.8x when compared to Coconut [NDSS 2019], the state-of-the-art AC scheme for blockchains. This translates to a reduction in transaction fees from 94 USD to 8 USD on Ethereum in August 2022. However, 8 USD is still high for most applications, and ZEBRA further drives down credential verification costs through batched verification. For a batch of 512 layer-1 and layer-2 wallets, the gas cost is reduced by 35x and 641x on EVM, and the transaction fee is reduced to just 0.23 USD and 0.0126 USD on Ethereum, respectively. For perspective, these costs are comparable to the minimum transaction costs on Ethereum. |
|---|---|
| Year | 2022 |
| Link to the paper | https://eprint.iacr.org/2022/1286 |
| Relevance score | Relevant |
| Quality score | 4 |
| Labels | Anonymous CredentialsImplementations |
ZEBRA - Zero-knowledge (Anonymous), batched, revocable and auditable credentials
ZEBRA supports -
- Auditability - Authorized auditors identify the owner of a maliciously behaving user.
- Revocation - as credentials are often lost or stolen, and credentials of malicious users need to be revoked.
- On-chain verification - With the primary goal of minimizing the verification cost using ZK-SNARKs. ZEBRA further reduces the cost of credential verification through batched verification.
Note: Batched verification relies on an untrusted aggregator to verify many credential verification proofs and recursively prove their validity to the contract with a single SNARK proof, the cost of which is amortized across multiple users.
System Model
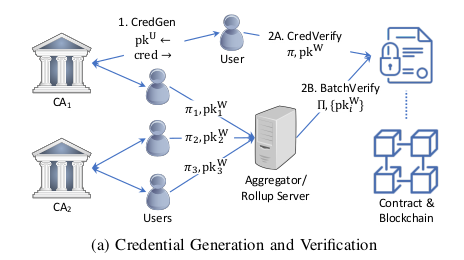
Source: This paper
- Credential Verification Smart Contract:
- This smart contract is responsible for verifying a credential (protocols 2A and 2B) and issuing an on-chain access token to the nominated wallet corresponding to the user.
- These tokens can then be efficiently checked by the smart contract of the access-controlled application before granting access to the wallet.
- It also stores the list of approved CAs and their revocation lists.
- Users:
- Users can obtain a credential cred associated with their public-key from any approved by the access-controlled application if the user satisfies the issuance policy (protocol ).
- They can then prove on-chain that they hold a valid credential in a privacy-preserving way by providing a proof to get an access token for their wallet (protocol ).
- We assume users are malicious and can act arbitrarily to get verified without holding a valid credential.
- Certificate Authorities (CAs):
- CAs are organizations trusted to issue credentials to users if they satisfy the application’s credential issuance policy (protocol 1).
- A CA can revoke a credential it issued by adding its unique identifier to the revocation list (protocol ).
- They also help auditors in deanonymizing malicious users of their issued credentials (protocol ).
- We assume the s are trusted for integrity since they are reputed organizations authorized by the application.
- Aggregator/Rollup Server:
- The aggregator/rollup server is an untrusted party that batches credential verification transactions for and wallets, respectively, to reduce on-chain verification costs.
- By sending a short proof to the contract which ensures that the server knows a valid credential verification proof for each in the batch (protocol ).
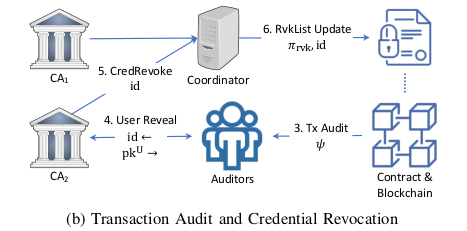
Source: This paper
- Auditors:
- Auditors can audit a credential verification transaction via its associated audit token if a majority of them agree to it (protocol ).
- The audit reveals a unique credential identifier that embeds the CA that issued it.
- Auditors then share with the issuing CA, and the CA deanonymizes the user by sending its user’s public key or any other identity information to the auditors (protocol ).
- ZEBRA can handle a minority of malicious auditors.
- Contract Coordinator:
- The coordinator is responsible for managing the credential verification contract.
- Its responsibilities are updating the list of approved CAs according to the access policy.
- Batched updates to revocation lists of all CAs.
- No need to trust the coordinator to post correct updates to the revocation list and require that it provide a proof ensuring that it knows a valid signature from the CA associated with the credential identifier it is adding to the revocation list (protocol ).
Preliminaries
- zk-SNARKs: zk-SNARK is a tuple of three algorithms:
- Setup : On input security parameter and relation , outputs a common reference string .
- Prove : On input and a statement-witness pair , outputs a proof .
- Verify: On input , statement and proof , outputs a bit to indicate if the proof is valid.
Authors also use simdSNARK to denote a “data-parallel” SNARK which takes as input multiple statement-witness pairs and outputs a single succinct proof .
- Digital Signature: The signature schemes that are existentially un-forgeable under chosen message attacks (EUF-CMA). They consists of three algorithms
- Gen: on input security parameter , outputs a secret key and a public verification key .
- Sign: on input sk and message , output signature .
- Verify: on input , and , outputs if is a valid signature for w.r.t. .
- Threshold Public-Key Encryption (TKPE): Use threshold public key encryption (TPKE) satisfying the simulation based IND-CCA2 security notion defined in TKPE.
- Setup : on input threshold for parties, outputs the public key and verification key , along with secret keys for each party.
- Enc: encrypts message under public key using randomness .
- Dec : computes a partial decryption of .
- Verify: checks whether was correctly computed using and .
- Combine : recovers message given partial decryptions which verify successfully.
- Merkle Trees : The sparse merkle trees SMT are authenticated data structures MT on key-value pairs supporting the following operations -
- Add : inserts a key-value pair in MT . If the key already exists, the value is updated.
- Root : outputs the current merkle-root of MT.
- MProve : outputs a membership proof for key .
- MVerify : on inputs root , key , value and proof , outputs if exists in .
- NMProve : outputs a non-membership proof for key .
- NMVerify : on inputs root , key and proof , outputs if does not exist in .
Definitions
Anonymous Credential Scheme
1. Credential Generation
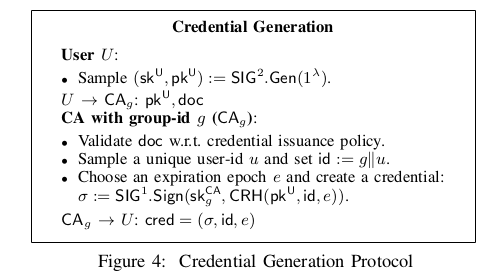
Example: A user provides a identity document (Driver’s Licence or Passport, etc) issued by a Government authority and his/her public key to get a credential from CA.
Note: In a real system there are far fewer users than the number of public keys. We leverage this by using compact 40 -bit identifiers as opposed to 256 -bit public keys, which in turn reduces the credential verification circuit size and also leads to smaller on-chain storage costs during revocation.
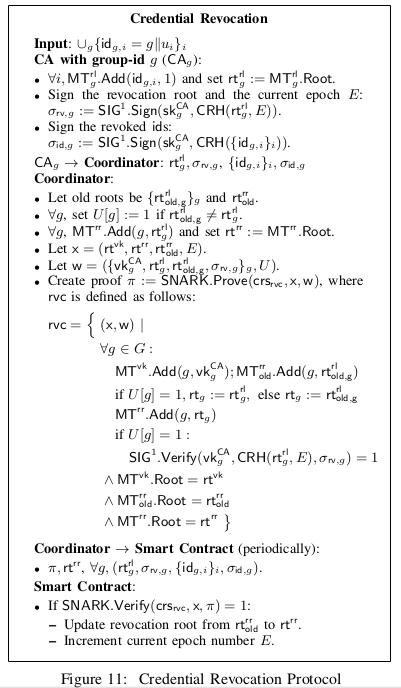
2. Credential Revocation
- : stores credential identifiers revoked by
- : stores merkle-roots of each CA’s revocation list
The coordinator then locally updates and creates a proof attesting to the correctness of new revocation root :
- , known by the contract, is the old root of revocation merkle tree with as leaves.
- , provided by the coordinator, is the new root of revocation merkle tree with as leaves.
- , known by the contract, is the root of CA’s verification key merkle tree with as leaves.
- s.t. , I know a signature on w.r.t. , where is the current epoch number.
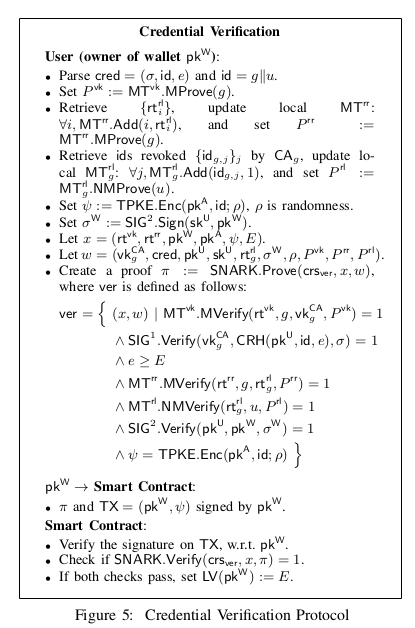
3. Credential Verification
- A user owning a credential cred from a CA, say , can use it to issue an ephemeral access token for any wallet it owns.
- The audit token is simply an encryption of the unique credential identifier corresponding to the credential used for verification.
- These tokens are checked by the access-controlled application before granting access and they are only valid for one epoch.
- Epoch number incremented when revocation list updated.
- Access token verification is done by checking if the epoch identifier matches the current epoch.
- The contract maintains a hash-map that maps wallet addresses to the epoch when they are last verified, i.e. .
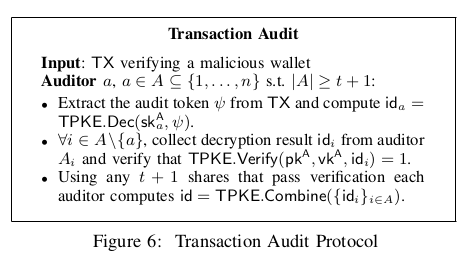
4. Transaction Audit
- A threshold number out-of- of auditors can deanonymize the user associated with a wallet, if they deem the wallet has displayed malicious behaviour.
- Since access token encrypts using the public key of the auditors, t+1 of them can collaboratively decrypt to recover .
- When this points the auditors to the issuing , who can then reveal user’s identity and revoke the corresponding credential if required.
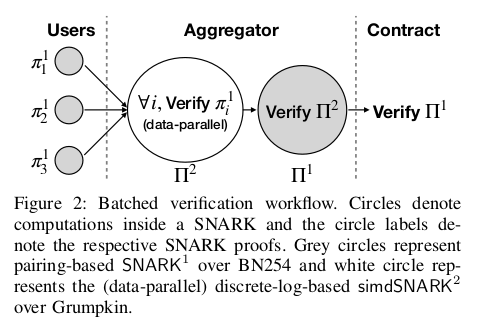
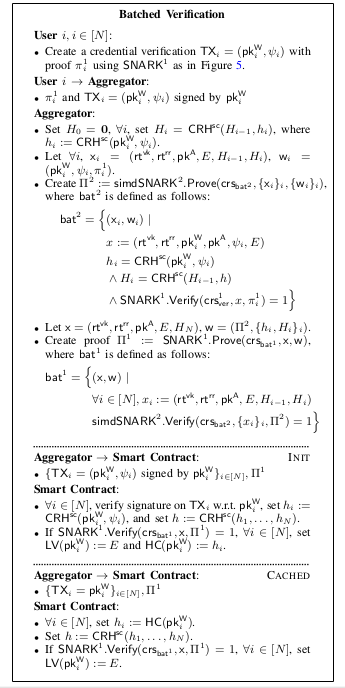
5. Batched Verification
- Authors instantiate with pairing-based Groth16 (over BN254)
- with discrete-log-based Spartan (over Grumpkin) optimized for data-parallelism.
- Both of these SNARKs use R1CS arithmetization.
Source: This paper
Batching solution works as follows with two layers of recursion -
- A batch of users independently create credential verification proofs using , and send them along with transaction data to the aggregator.
- First, the aggregator verifies the proofs using to output .
- Then the aggregator verifies using to output , which is then sent to the contract for batched verification along with .
- Finally, the contract processes and verifies to ensure the validity of user proofs before updating access tokens for , i.e, .
Conclusion
- ZEBRA supports auditability and revocation
- ZEBRA relies on ZK-SNARKs for reducing the on-chain verification costs and batch credential verifications.
References
- ZEBRA: Anonymous Credentials with Practical On-chain Verification and Applications to KYC in DeFi, https://eprint.iacr.org/2022/1286.