NSSIA: A New Self-Sovereign Identity Scheme with Accountability
| Abstract | Self-sovereign identity (SSI) is a new distributed method for identity management, commonly used to address the problem that users are lack of control over their identities. However, the excessive pursuit of self-sovereignty in the most existing SSI schemes hinders sanctions against attackers. To deal with the malicious behavior, a few SSI schemes introduce accountability mechanisms, but they sacrifice users’ privacy. In addition, the digital identities (static strings or updatable chains) in the existing SSI schemes are as inputs to a third-party executable program (mobile app, smart contract, etc.) to achieve identity reading, storing and proving, and users’ self-sovereignty are weakened. To solve the above problems, we present a new self-sovereign identity scheme to strike a balance between privacy and accountability and get rid of the dependence on the third-party program. In our scheme, one and only individual-specific executable code is generated as a digital avatar-i for each human to interact with others in cyberspace without a third-party program, in which the embedding of biometrics enhances uniqueness and user control over their identity. In addition, a joint accountability mechanism, which is based on the shamir (t, n) threshold algorithm and a consortium blockchain, is designed to restrict the power of each regulatory authority and protect users’ privacy. Finally, we analyze the security, SSI properties and conduct detailed experiments in terms of the cost of computation, storage, and blockchain gas. The analysis results indicate that our scheme resists the known attacks and fulfills all the six SSI properties. Compared with the state-of-the-art schemes, the extensive experiment results show that the cost is larger in server storage, blockchain storage, and blockchain gas, but is still low enough for practical situations. |
|---|---|
| Year | 2022 |
| Link to the paper | https://www.hindawi.com/journals/scn/2022/1607996/ |
| Relevance score | Maybe relevant |
| Quality score | 3 |
| Labels | Decentralized identityImplementationsManagement of credentialsSybil resistance insightsVerifiable Credentials |
The following are the contributions of the proposed scheme:
- NSSIA introduces executable code that enables users to completely control their identities through self-sovereign identity.
- The user's biometrics are embedded into one and only one executable code, thereby eliminating the dependency on third-party programs. Users can store, read, and prove their identities with network servers using their own local executable code, which uses the hash of the executable code as an identifier. To denote the executable code focusing on digital identity, they have borrowed the term "digital avatar" from metaverse and reformed it to "digital avatar-i.".
- As part of a joint accountability mechanism, which decentralizes the authority of regulatory authorities and hides users' information in reality through shamir(t, n) threshold signature algorithms, a consortium blockchain is introduced to ensure an impartial audit without violating privacy.
- A security analysis, SSI properties in generation phase, and extensive experiments on storage, computation, and blockchain gas costs are provided for the proposed scheme.
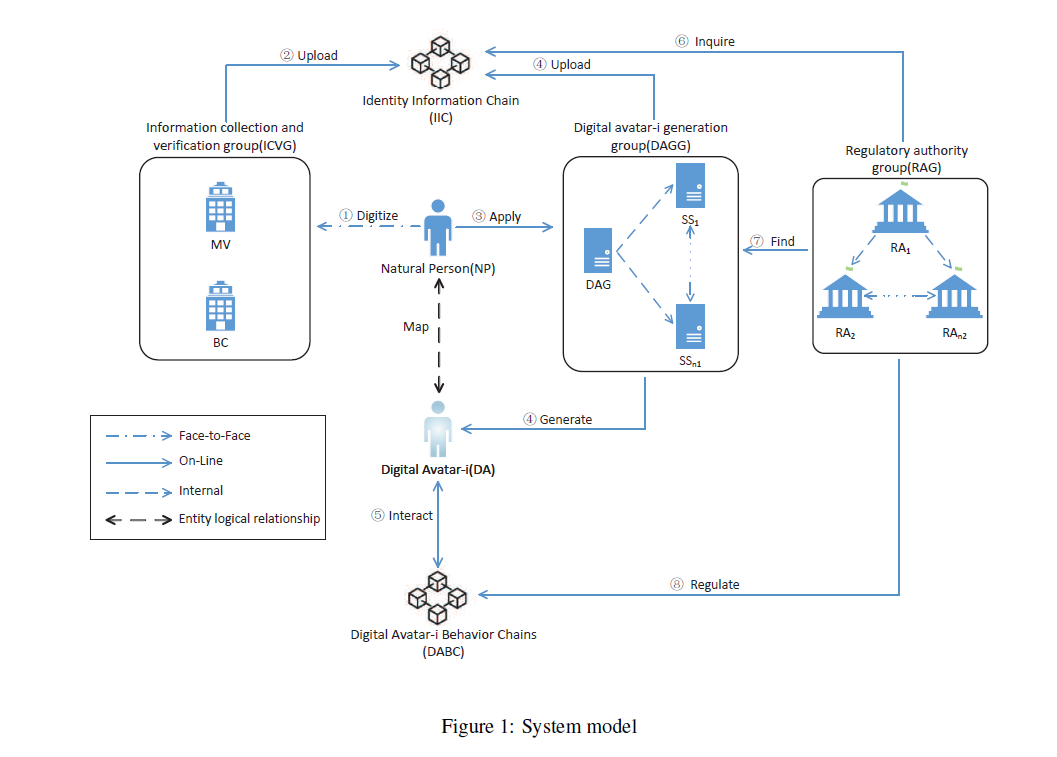
Their system model consists of seven entities:
- NP, Natural Person, is an individual living in the physical world. With the ICVG, he/she can digitally represent himself/herself and apply for a DA with the DAGG.
- DA, Digital Avatar-i, is an executable program that focuses on the identity dimension of digital avatars. A digital avatar represents a living person to interact with others in cyberspace, and has one-to-one relationships with NP.
- ICVG, Information Collection and Verification Group, verifies the person requesting the service is the only one alive and provides that service for him/her. There are two types of entities in this system: metadata verifiers (MV) and biometric collectors (BC). By providing metadata, such as a name, ID number, and address, MV proves that the requestor exists in physical space. Two types of biometric data are collected by BC: one is for permanent proof and the other is for activating DAs.
- IIC, Identity Information Chain, is a consortium blockchain. The purpose of this is to record proof of physical identity information (metadata and biometric data), to calculate the hash of DA, and to ensure that each NP only has one proof.
- DAGG, Digital Avatar-i Generation Group, generates a unique DA for each NP. There are two types of entities in it: a digital avatar-i generator (DAG) and a secure storages (SSs). Initially, DAG verifies an applicant's identity by using the IIC data, and then generates a sole DA. The metadata of NP and the hash of DA are safely stored in SSs that contain , which rely on threshold algorithms.
- DABC, Digital Avatar-i Behavior Chain, is an infrastructure that includes multiple blockchains and supports all kinds of decentralized applications (Dapps). In cyberspace, these Dapps provide services for DAs, and the DABC keeps historical records of these services.
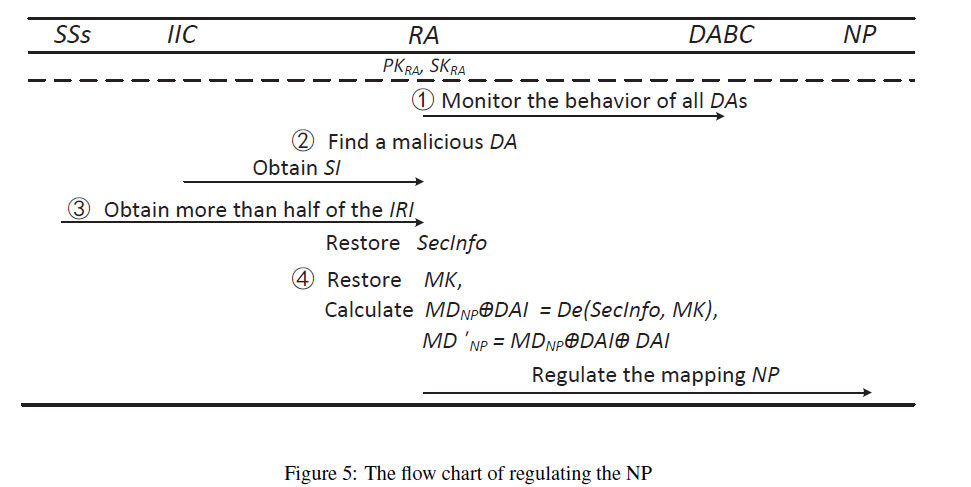
- RAG, Regulatory Authority Group, regulates NP by monitoring the actions of the DA in the DABC. The system consists of n regulatory authorities , where at least three of them can hold suspicious users accountable.
Proposed NSSIA
Initialization
A master key (MK) and subkeys (SubKs) are generated during initialization by the IIC. Additionally, RAG, DAGG, and ICVG generate their public and private keys.
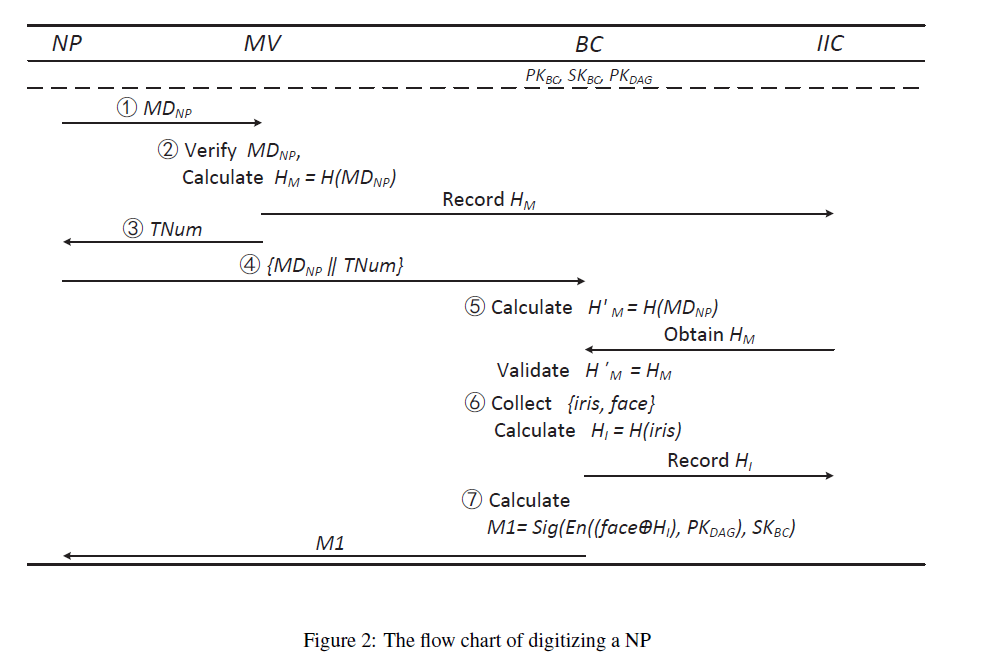
Digitization
For the generation of the DA, the NP sends the metadata to the ICVG. The MV verifies the metadata and submits the proof to the IIC. A BC collects the NP's biometric data, sends the proof of the biometric data to the IIC, and then sends the NP a digitization credential.
Generation
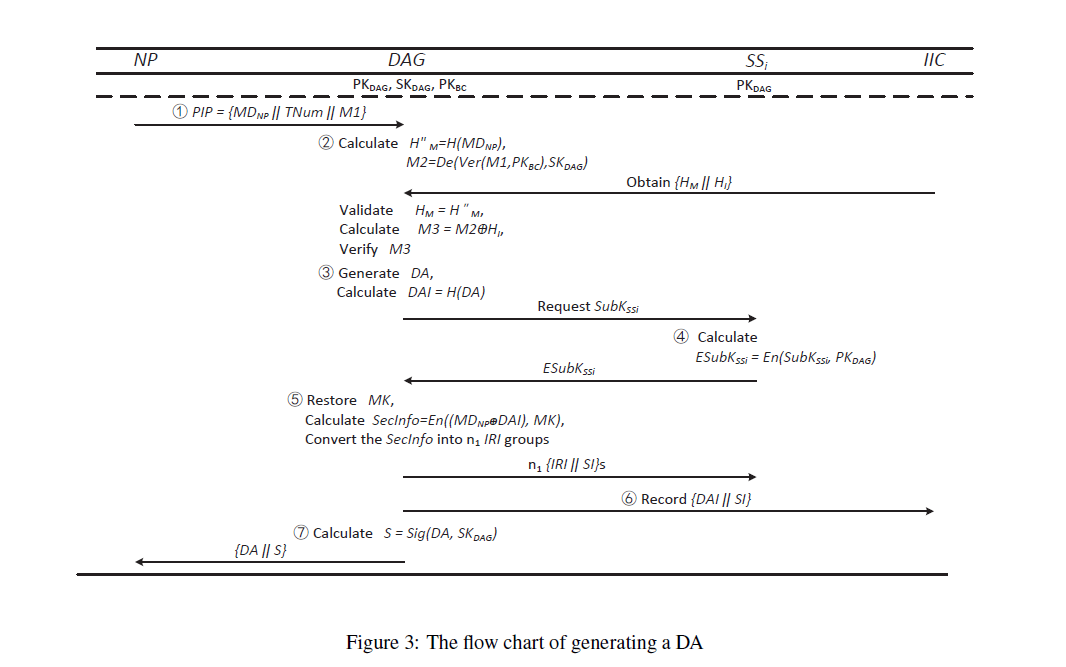
The DAGG can generate a DA for the NP after digitization, and it consists of seven steps.
- As a first step, the NP applies for a DA to the DAGG.
- Second, the DAG verifies NP's identity using the proof information in the IIC.
- A third step is for the DAG to generate a DA and request the subkeys of the SSs.
- DAG receives the encrypted subkeys from the SSs.
- A DAG then restores the MK, splits it into multiple backups, and creates SecInfo.
- Finally, the DAG sends the DA to the NP after recording the proof in the IIC.
Interaction
A NP can access various services provided by Dapps built on DABC after receiving a DA. A live face recognition is used at first to activate the DA by the NP. After that, the activated DA may select the DAI or a random string as the identifier for the NP to participate in cyberspace activities.
Accountability
Whenever there is a malicious behavior on the part of a DA, the RAG can identify the mapping NP by requesting the IIC and finding the metadata of the NP in the DAGG using the joint participation of multiple RAs. As a result, the RAG will be able to regulate all the historical behavior of the malicious NP.