EBSI (joint initiative from the European Commission and the European Blockchain Partnership)
| Abstract | This playbook presents the DIDs and Verifiable Credentials technology that is built on EBSI. EBSI is a joint initiative from the European Commission and the European Blockchain Partnership. ``The vision is to leverage blockchain to accelerate the creation of cross-border services for public administrations and their ecosystems to verify information and to make services more trustworthy.'' ``Since 2020, EBSI has been deploying a network of distributed nodes across Europe, supporting applications focused on selected use cases.'' (abstracts from https://ec.europa.eu/digital-building-blocks/wikis/display/EBSI/Home) |
|---|---|
| Year | |
| Link to the paper | https://ec.europa.eu/digital-building-blocks/wikis/display/EBSIDOC/EBSI+Verifiable+Credentials+Playbook |
| Relevance score | Relevant |
| Quality score | N/A |
| Labels | Decentralized identityGood reference sourceImplementationsSelf-sovereign identityVerifiable Credentials |
We have rated this playbook as ``relevant'' because (i) it explains the DID format according to the W3C standard and it provides some interesting insights regarding various DID methods that can be used for the issuer and the user in a Verifiable Credential system. (ii) it is an application of Verifiable Credentials.
The disadvantage of their construction for our case is that the issuer needs to digitally sign.
W3C DIDs and Verifiable Credentials based on the European Blockchain Framework (EBSI)
The Verifiable Credentials will be used so that the citizens can prove claims about their identities to public administrations and businesses.
A trusted issuer issues the Verifiable Credential (VC), and the holder stores the VC in a digital wallet and can present it to a verifier.
DIDs format according to W3C standard
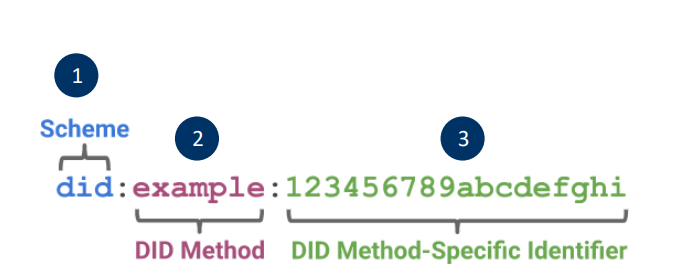
It consists of three parts.
- The first part is ``did''.
- The second part is the DID method that is used. For example in this case this part is ``ebsi''.
- The third part is a unique random string whose generation depends on the DID method.
DIDs format in EBSI framework.
- The second part is ebsi.
- The third part is constructed using two different methods: the first method is used for Legal Entities (LE), who will be the issuers of the Verifiable Credentials and the second one is used for Natural Persons (NP) who will be the holders of the credentials (or users).
.
DID method for the issuer
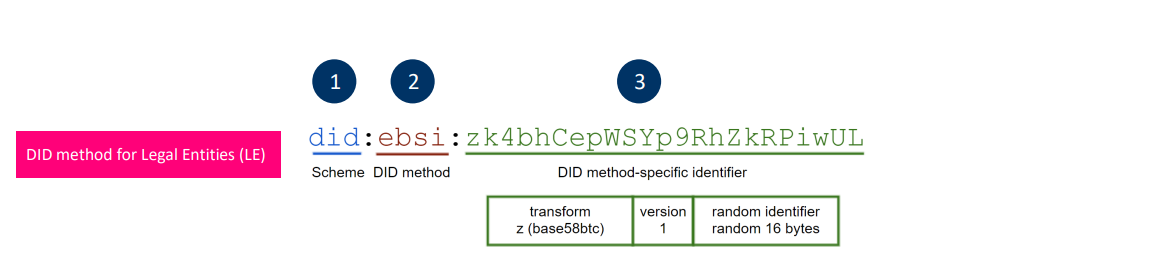
- It supports frequent public key recovery: this means that the issuer can update frequently its public key without changing DID. The issuer creates a DID document that includes its public key and updates it when it changes its public key*.
- The DIDs and DID documents are recorded on the ebsi ledger.
- The issuer holds a DID control key that it can use to update its DID document.
- The issuer can publish on the ebsi ledger a list of the revoked public keys.
- The generation of the DIDs and DID documents is made by a wallet-like application or back office application.
* A trusted accreditation authority checks if the issuer holds the private keys for the public keys in the DID document and creates an issuer register, a list with all the approved issuers along with the certificates they can sign.
DID method for the holder
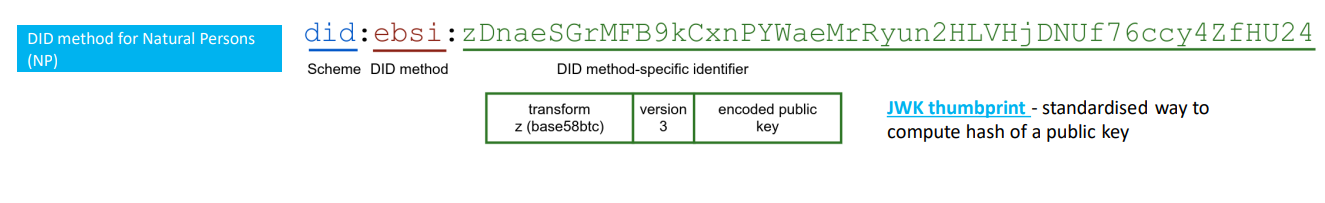
- The DIDs and the DID documents are generated by a digital wallet.
- The DID documents are stored in a digital wallet, they are not recorded on the ebsi ledger.
- It is connected with the public key of the holder.
The Issuance of the Verifiable Credential
- The issuer creates its DID and DID document (which includes its public keys), and posts it on the ebsi ledger. This DID is connected with a DID control key.
- A trusted accreditation authority checks if the issuer holds the private keys for the public keys on the DID document, and creates an issuer register, a list with all the approved issuers along with the certificates they can sign.
- The issuer can post on the ebsi ledger a CRL (certificate revocation list) or a list with revoked public keys.
- The holder communicates with the issuer via OPENID connect protocol.
- The holder authenticates himself with the issuer. The issuer checks if the holder is the owner of the private key connected to the DID.
- The issuer signs the verifiable credential.
- The holder stores this credential in the digital wallet.
Verifiable Credential
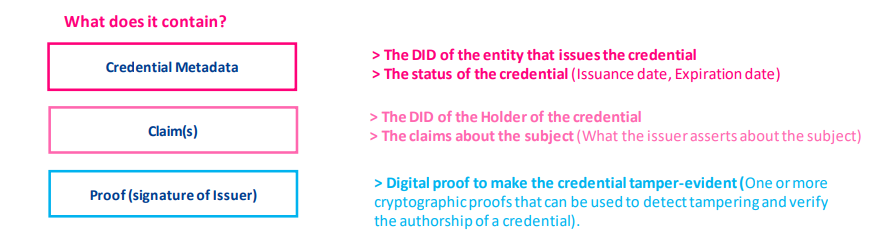
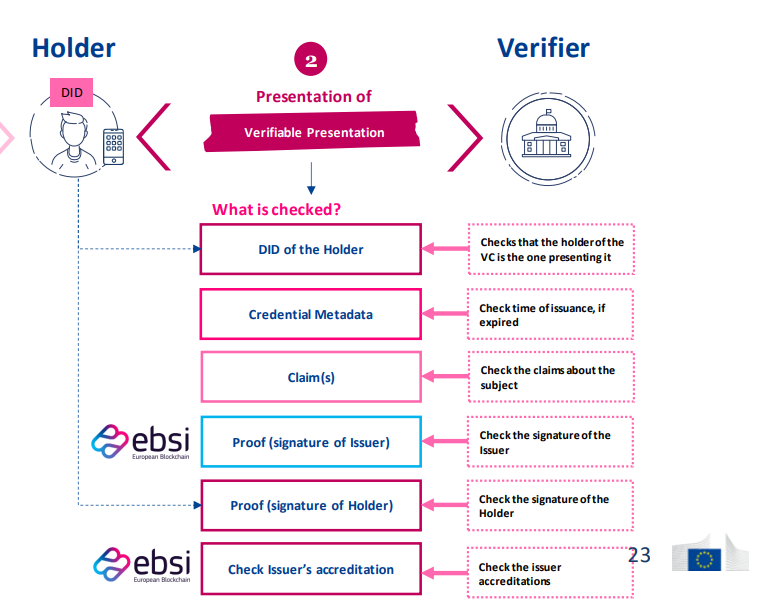
Verifiable Credential Presentation
- The verifier has a verifier app that can interact with the wallet and EBSI ledger.
- The verifier asks the holder to prove that it knows the private key for the public key that is connected with its DID.
- The verifier verifies the signature of the issuer and checks that the public key has not been revoked.
References
- EBSI Verifiable Credentials https://ec.europa.eu/digital-building-blocks/wikis/display/EBSIDOC/EBSI+Verifiable+Credentials+Playbook
- EBSI: European blockchain https://ec.europa.eu/digital-building-blocks/wikis/display/EBSI/Home
- Verifiable Credentials Data model v1.1, W3C recommendation https://www.w3.org/TR/vc-data-model/
- Jones, M., and N. Sakimura. JSON Web Key (JWK) Thumbprint . No. rfc7638. 2015.
- Chadwick, Kenichi Nakamura, and Jo Vercammen. "OpenID for Verifiable Credentials." (2022).