DECO
| Abstract | Thanks to the widespread deployment of TLS, users can access private data over channels with end-to-end confidentiality and integrity. What they cannot do, however, is prove to third parties the provenance of such data, i.e., that it genuinely came from a particular website. Existing approaches either introduce undesirable trust assumptions or require server-side modifications. As a result, the value of users' private data is locked up in its point of origin. Users cannot export their data with preserved integrity to other applications without help and permission from the current data holder. We propose DECO (short for decentralized oracle to address the above problems. DECO allows users to prove that a piece of data accessed via TLS came from a particular website and optionally prove statements about such data in zero-knowledge, keeping the data itself secret. DECO is the first such system that works without trusted hardware or server-side modifications. DECO can liberate data from centralized web-service silos, making it accessible to a rich spectrum of applications. To demonstrate the power of DECO, we implement three applications that are hard to achieve without it: a private financial instrument using smart contracts, converting legacy credentials to anonymous credentials, and verifiable claims against price discrimination. |
|---|---|
| Year | 2019 |
| Link to the paper | https://www.deco.works/ |
| Relevance score | Very relevant |
| Quality score | 5 |
| Labels | ImplementationsLegacy compatibleManagement of credentialsPossible tool in larger solutionSybil resistance insights |
TL;DR
DECO is a protocol that enables users to prove (potentially in zero-knowledge) to a verifier that he pulled a piece of data from a certain web server via a TLS channel. Unlike Town Crier or TLS-N, it works without trusted hardware or modification on the server side.
The main idea is to share the client keys among the prover and the verifier so that they can jointly act as a single client like in a standard TLS protocol. Note that a server cannot distinguish whether it interacts with a client of a TLS session or a tuple of prover and verifier in a DECO protocol.
Preliminary
Roles
- Server(): Data source which supports the TLS protocol.
- Prover(): Off-chain repeater that requests data from the server, generates a proof of validity, then sends it to the verifier.
- Verifier(): On-chain Oracle node, receives the data and proof from the prover and verifies its correctness.
Notation
- : the session ID, unique per session.
- : randomly generated bit string.
- : query information.
- : response information.
- : signature.
- : MAC tag.
Transport Layer Security (TLS) protocol
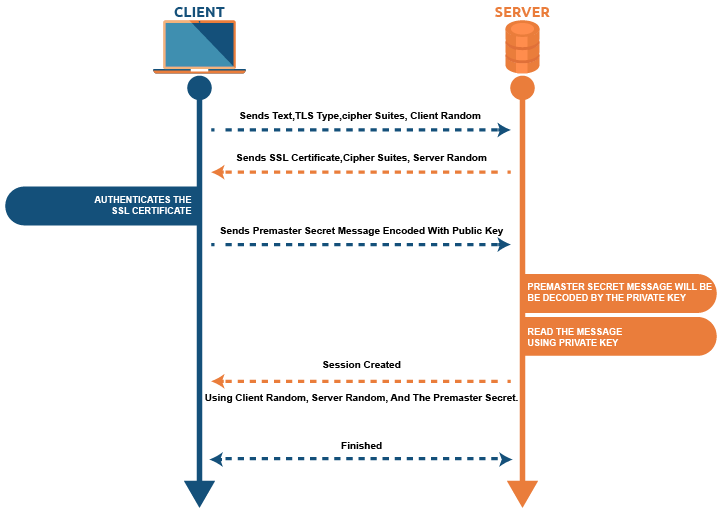
- The client sends “client hello” to the server, along with TLS type, and cipher suite with a random generated by the client.
- The server receives the data, and sends “server hello” to the client, along with a certificate, cipher suite with a random generated by the server, and the server’s public key .
- The client receives the data, and generates a random premaster secret , encrypts it with , and sends it to the server.
- The server using the secret key decrypts the message and obtains . For both server and client, the session key is .
- The server uses the session key with symmetric encryption to encrypt the handshake completes the message and sends it to the client. TLS handshake complete.
DECO Protocol
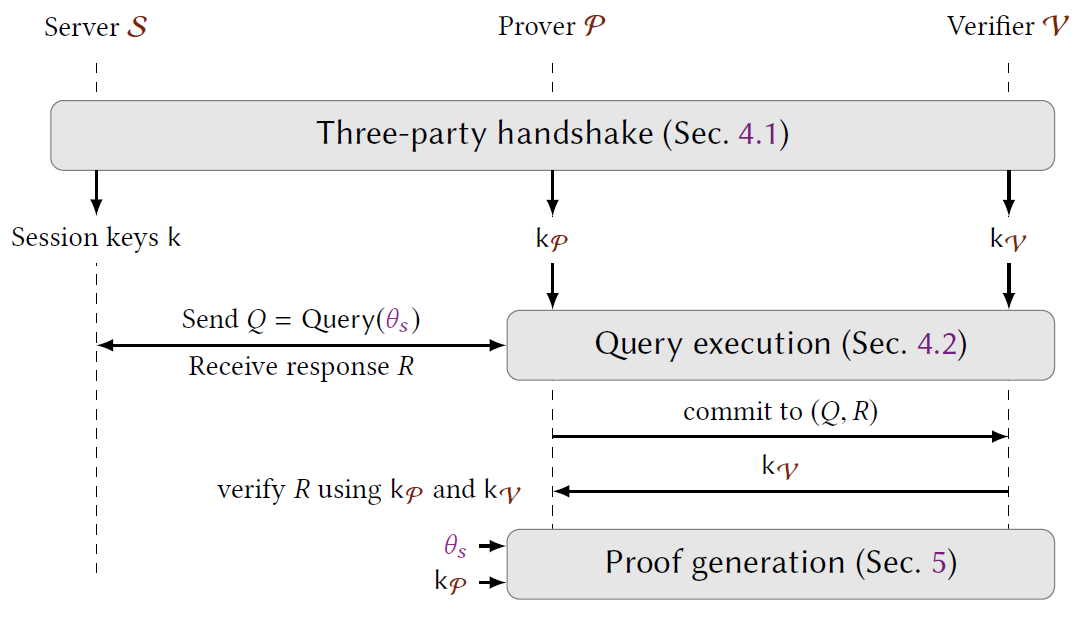
Trigger:
- Verifier () is asked for off-chain data,
- generates a session ID (), a query template (), and a statement () to be proven.
- sends to .
Three-party handshake
The goal of the three-party handshake is to run a TLS handshake protocol, which for the server () side is just following the standard TLS protocol, but the prover () and verifier () use a separated key which can be combined to communicate with the server. (All additions and multiplications are Elliptic Curve operations)
- sends “client hello” to , along with TLS type, cipher suite with a random generated by .
- receives the data, sends “server hello” to , along with certificate , cipher suite with a random generate by the server, and server’s public key and a signature over .
- verifies that is valid and is valid over , then sends to . Then checks the same thing also.
- and jointly generate a private key:
- generates a secret , calculates the verifier premaster key , and sends to .
- generates a secret , calculates the prover premaster key , runs the key exchange procedure, and sends to after encrypting with .
- an run to compute a sharing of x-coordinate of , denoted as and .
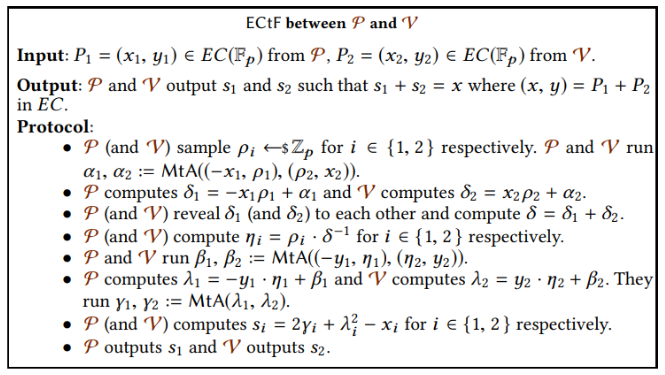
Source: https://arxiv.org/abs/1909.00938
- and send and to (see below figure) to compute and , send to and respectively, which is and .
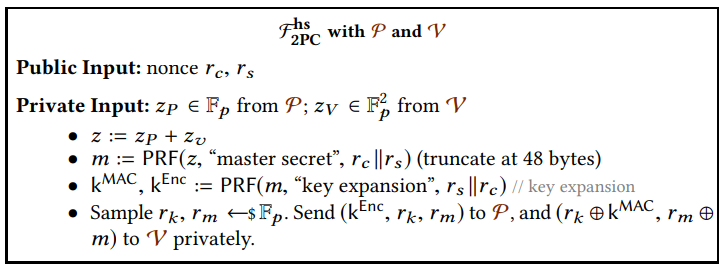
Source: https://arxiv.org/abs/1909.00938
- computes a hash of the handshake messages, and runs a 2PC-PRF with to compute “client finished”, sends to .
- computes “server finished”, sends it to , then and recompute and check if “server finished”, and abort if not. Three-party handshake complete.
Note that at the end of the three-party handshake,
- obtains and ,
- obtains .
Query execution
- constructs the query using the template , is some secret parameter stored in , e.g. API key, password, etc.
- invokes 2PC-HMAC with to compute a tag which signs the query message , sends to . (The goal of this step is to ensure that the content of the query is not been manipulated by ).
The goal of 2PC-HMAC is to compute , which is the following equation, where is repeated and is repeated.
- and input and to run a 2PC to compute , and reveal to , where denotes a compression hash function of SHA256 and is an initialization vector. Note that is computed once in a TLS session.
- computes the inner hash , which represents in the above equation.
- inputs , and inputs to run a 2PC to compute , which outputs .
Commit and verify:
- sends to .
- responds to with ,
- sends to , (note that now has the , so it cannot be altered)
- then sends back .
- computes , decrypts , and verifies with
Proof generation
- Define which is a statement about the response (e.g: “Alice has more than $3000 in the bank balance”), , , sends to ZKP function .
- constructs a relation , which is if and only if:
- and are the ciphertexts of and under and .
-
-
- sends to .
- checks if , and verifies the proof .
Assessment
DECO would allow a user to prove, in zero-knowledge, that some information comes from a specific TLS session with a specific server, and further that this information is taken from the right context. If such a tool were implemented, it would be of paramount importance for the transport of Web2 data to Web3. We label it as very relevant.
References