Coconut: Threshold Issuance Selective Disclosure Credentials with Applications to Distributed Ledgers
| Abstract | Coconut is a novel selective disclosure credential scheme supporting distributed threshold issuance, public and private attributes, re-randomization, and multiple unlinkable selective attribute revelations. Coconut integrates with blockchains to ensure confidentiality, authenticity and availability even when a subset of credential issuing authorities are malicious or offline. We implement and evaluate a generic Coconut smart contract library for Chainspace and Ethereum; and present three applications related to anonymous payments, electronic petitions, and distribution of proxies for censorship resistance. Coconut uses short and computationally efficient credentials, and our evaluation shows that most Coconut cryptographic primitives take just a few milliseconds on average, with verification taking the longest time (10 milliseconds). |
|---|---|
| Year | 2018 |
| Link to the paper | https://arxiv.org/pdf/1802.07344.pdf |
| Relevance score | Relevant |
| Quality score | 5 |
| Labels | PermissionlessSmart Contracts instead of oracles |
About Coconut
Coconut is a selective disclosure credential scheme that supports:
- Distributed threshold issuance
- Public and private attributes
- Re-randomization - protecting privacy even in the case in which all authorities and verifiers collude
- Multiple unlinkable selective attribute revelations
Overview of Coconut
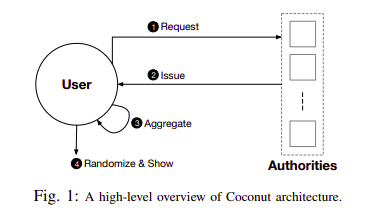
- Any Coconut user may send a Coconut request command to a set of Coconut signing authorities; this command specifies a set of public or encrypted private attributes to be certified into the credential.
- Each authority answers with an issue command delivering a partial credential.
- Any user can collect a threshold number of shares, aggregate them to form a single consolidated credential and re-randomize it.
- The user who owns the credentials can then execute the show protocol to selectively disclose attributes or statements about them. The showing protocol is publicly verifiable and may be publicly recorded.
The design Goals of Coconut
- Threshold authorities: Only a subset of the authorities is required to issue partial credentials in order to allow the users to generate a consolidated credential. The communication complexity of the request and issue protocol is . Where is the subset of authorities.
- Non-interactivity: The authorities may operate independently of each other, i.e., following a simple key distribution and setup phase, they do not need to synchronize or further coordinate their activities.
- Blindness: The authorities issue the credential without learning any additional information about the private attributes included in the credential.
- Unlinkability: It is impossible to link multiple showings of the credentials with each other, or the issuing transcript, even if all the authorities collude.
- Liveness: Coconut guarantees liveness as long as the threshold number of authorities is honest.
- Efficiency: After aggregation and re-randomization, the attribute showing and verification involve only a single consolidated credential, and are therefore in terms of both cryptographic computations and communication of cryptographic material.
- Short credentials: Each partial credential and the consolidated credential is composed of exactly two group elements, no matter the number of authorities or the number of attributes embedded in the credentials.
Cryptographic primitives
- Zero-knowledge proofs:
- Bilinear-map: Coconut requires groups of prime order with a bilinear map satisfying Bilinearity and non-degeneracy properties.
- A cryptographically secure hash function .
Coconut scheme definition
- Setup: defines the system parameters with respect to the security parameter . These parameters are publicly available.
- KeyGen: is run by the authorities to generate their secret key and verification key from the public .
- AggKey: is run by whoever wants to verify a credential to aggregate any subset of verification keys into a single consolidated verification key . AggKey needs to be run only once.
- IssueCred: is an interactive protocol between a user and each authority, by which the user obtains a credential embedding the private attribute satisfying the statement .
- AggCred: is run by the user to aggregate any subset of partial credentials into a single consolidated credential .
- ProveCred: is run by the user to compute a proof of possession of a credential certifying that the private attribute satisfies the statement .
- VerifyCred: is run by whoever wants to verify a credential embedding a private attribute satisfying the statement , using the verification key and cryptographic material generated by ProveCred.
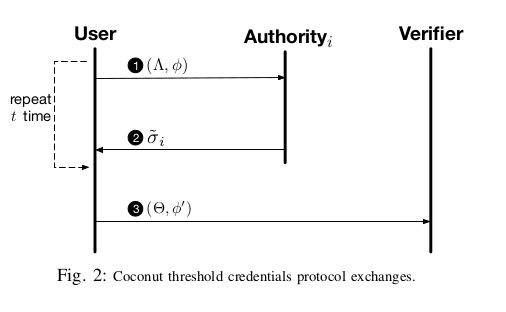
The Coconut Threshold Credential Scheme construction
The Coconut threshold credential scheme allows users to obtain a partial credential on a private or public attribute . In a system with authorities, a -out-of- threshold credentials scheme offers great flexibility as the users need to collect only of these partial credentials in order to recompute the consolidated credential (both and are scheme parameters).
- Setup: Choose a bilinear group with order (-bit prime number). Let be generators of , and a generator of . The system parameters are .
- TTPKeyGen: Pick two polynomials of degree with coefficients in , and set . Issue to each authority a secret key , and publish their verification key .
This algorithm is executed by a trusted third-party or distributed key generation (DKG) scheme.
- IssueCred: Credentials issuance is composed of three algorithms:
- PrepareBlindSign: The users generate an El-Gamal key-pair ; pick a random , compute the commitment and the group element as follows:
Pick a random and compute El-Gamal encryption of as below:
Output , where is an application-specific predicate satisfied by m, and is defined by:
- BlindSign: The authority parses and . Recompute . Verify the proof using , and ; if the proof is valid, build and output ; otherwise output and stop the protocol.
- Unblind: The users parse and ; compute . Output .
- AggCred: Parse each as for . Output , where is the Lagrange coefficient:
- ProveCred: Parse and . Pick at random ; set ; build and . Output , where is an application-specific predicate satisfied by , and is:
- VerifyCred: Parse and σ' = (h' , s'); verify using and . Output true if the proof verifies, and ; otherwise output false.
Implementation
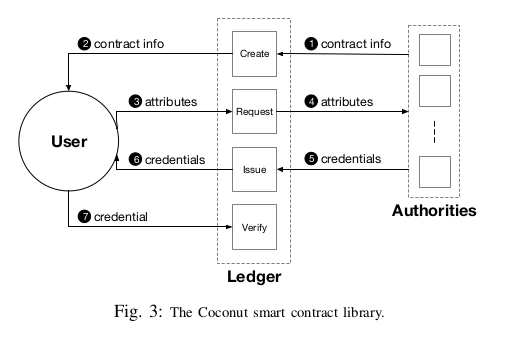
The smart contract has four functions, (Create, Request, Issue, Verify), as illustrated in the above Figure.
- First, a set of authorities call the Create function to initialize a Coconut instance defining the contract info; i.e., their verification key, the number of authorities, and the threshold parameter.
- The initiator smart contract can specify a callback contract that needs to be executed by the user in order to request credentials; e.g., this callback can be used for authentication.
- Any user can request a credential through the Request function by executing the specified callback contract and providing the public (clear texts) and private attributes to include in the credentials.
- Each signing authority monitors the blockchain at all times, looking for credential requests. If the request appears on the blockchain (i.e., a transaction is executed), it means that the callback has been correctly executed.
- Each authority issues a partial credential on the specified attributes by calling the Issue procedure.
- In this implementation, all partial credentials are in the blockchain; however, these can also be provided to the user off-chain. Users collect a threshold number of partial credentials and aggregate them to form a full credential.
- Then, the users locally randomize the credential. The last function of the Coconut library contract is Verify which allows the blockchain —and anyone else— to check the validity of a given credential.
Limitation: It is not efficient for the authorities to continuously monitor the blockchain.
- Authors implement a smart contract library in Chainspace to enable other application-specific smart contracts to conveniently use our cryptographic primitives.
- The authors also implement an Ethereum smart contract library in solidity. This library is written using Ethereum’s pre-compiled smart contract for point addition and scalar multiplication in , whereas Coconut requires operations on to verify credentials. The authors also implemented addition and scalar multiplication on as an Ethereum smart contract library.
- Integration of Coconut into Hyperledger Fabric —a permissioned blockchain platform— is straightforward. Fabric contracts run on private sets of computation nodes—and use the Fabric protocols for cross-contract calls. In this setting, Coconut issuing authorities can coincide with the Fabric smart contract authorities.
Applications
- Coin Tumbler
- Privacy-preserving petition
- Censorship-resistant distribution of proxies
Privacy-preserving petition
Authors consider the scenario where several authorities managing the country wish to issue some long-term credentials to its citizens to enable any third party to organize a privacy-preserving petition. There are three parties in this system:
- A set of signing authorities representing
- The citizens of
- A petition initiator
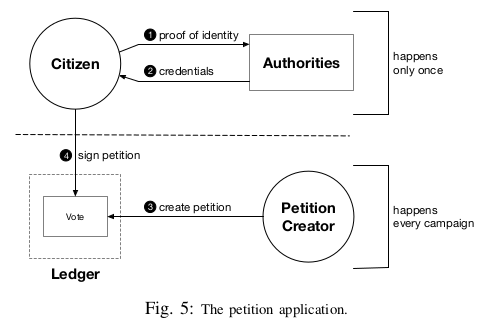
The signing authorities create an instance of the Coconut smart contract as described in the implementation section.
- The citizen provides a proof of identity to the authorities.
- The authorities check the citizen’s identity and issue a blind and long-term signature on her private key . This signature, which the citizen needs to obtain only once, acts as her long-term credential to sign any petition.
- Any third party can create a petition by creating a new instance of the petition contract and become the “owner” of the petition.
- The petition instance specifies an identifier unique to the petition
- is unlinkable to the other points of the scheme, as well as the verification key of the authorities issuing the credentials and any application-specific parameters (e.g., the options and current votes).
- This identifier can be generated through a hash function .
- In order to sign a petition,
- The citizens compute a value , is the attribute used in the credential issuance.
- They then adapt the zero-knowledge proof of the ProveCred algorithm of construction to show that is built from the same attribute in the credential.
- The petition contract checks the proofs and the credentials and checks that the signature is fresh by verifying that is not part of a spent list.
- If all the checks pass, it adds the citizens’ signatures to a list of records and adds to the spent list to prevent a citizen from signing the same petition multiple times (prevent double spending).
Remarks
- Threshold issuance of credentials through smart contracts and the scheme also supports blindness, unlinkability, and aggregability.
- On-chain verification of the credentials by two elliptic curve pairings checks.
- Limitations:
- Implementing the Coconut smart contract library on Ethereum is expensive as Ethereum does not provide pre-compiled contracts for elliptic curve arithmetic in .
- Adding and removing authorities implies to re-run the key generation algorithm for the threshold signature scheme.
References
- Coconut: Threshold Issuance Selective Disclosure Credentials with Applications to Distributed Ledgers, https://arxiv.org/pdf/1802.07344.pdf.