Anonymous credentials light
| Abstract | We define and propose an efficient and provably secure construction of blind signatures with attributes. Prior notions of blind signatures did not yield themselves to the construction of anonymous credential systems, not even if we drop the unlinkability requirement of anonymous credentials. Our new notion in contrast is a convenient building block for anonymous credential systems. The construction we propose is efficient: it requires just a few exponentiations in a prime-order group in which the decisional Diffie-Hellman problem is hard. Thus, for the first time, we give a provably secure construction of anonymous credentials that can work in the elliptic group setting without bilinear pairings and is based on the DDH assumption. In contrast, prior provably secure constructions were based on the RSA group or on groups with pairings, which made them prohibitively inefficient for mobile devices, RFIDs and smartcards. The only prior efficient construction that could work in such elliptic curve groups, due to Brands, does not have a proof of security. |
|---|---|
| Year | 2013 |
| Link to the paper | https://dl.acm.org/doi/10.1145/2508859.2516687 |
| Relevance score | Maybe relevant |
| Quality score | 4 |
| Labels | Anonymous CredentialsSignature scheme |
Introduction
This paper defines the notion of blind signatures with attributes that are based on Abe’s blind signature scheme [1] which is a modified version of the Schnorr scheme. In a blind signature with attributes, the signer and the user take a commitment to the user's attributes as input, and it outputs another (unlikable) commitment to the same attributes along with a signature on this commitment and a message of the user's choice. Note that taking the commitment to the user’s attributes as input gives the user the ability to prove in zero-knowledge that the committed data includes correct attributes.
Note that a blind signature with attributes can be used to construct an anonymous credential scheme as follows.
- A user with some attributes can generate a commitment to his attributes.
- He can prove in zero-knowledge that the commitment is generated from correct attributes.
- He runs a blind signature with attributes with commitment .
- Now he can convince any verifier that he has a credential that includes the desired attributes as follows:
- He presents his signature and the output commitment , and
- He proves in zero-knowledge that corresponds to those attributes.
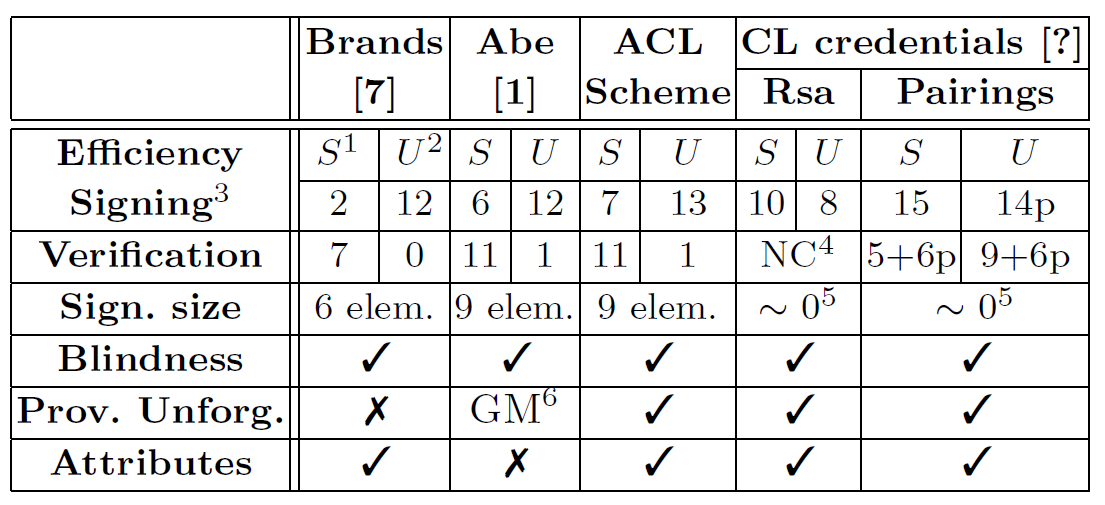
The importance of this paper is that it can work on the elliptic curve groups without pairings, which makes it more efficient. (see the below table)
Preliminary
OR-proof
An OR-proof is a -protocol for a relation in which the prover and the verifier have the common inputs and , and the prover knows an such that for .
Generalized Pedersen commitment
The Pedersen commitment is based on discrete logarithm assumption. This paper uses a generalized version of the Pedersen commitment scheme on the set of messages as follows:
- Setup: Assume that the security parameter is , and the maximum number of messages is . Let be a group with prime order with generators . Let be randomness.
- Commit: , where
Note that Pedersen commitment is information-theoretically hiding and computationally binding.
Combined commitment scheme
It is a combination of two commitments. For example, let us instantiate it with generalized Pedersen commitment. Assume that the generators are . Assume we have two commitments as follows:
-
-
Then the combined Pedersen commitment is
Blinded Pedersen commitment scheme
The Pedersen commitment can be made blinded by an additional parameter , where . Assume that we have a commitment . Then the value can be seen as a blinded Pedersen commitment, i.e.
Assumption
The security of the proposed scheme is based on the Decisional Diffie-Hellman assumption and the Discrete-Logarithm assumption.
Notation and setup
- Let be a group of order
- Let be a generator of
- Let be a hash function
- Assume a trusted party chooses as system parameters, where and is the maximum number of attributes that a user can have.
- The signer randomly selects a private key and computes his real public key .
- Given , the outputs which is the tag public key of the signer.
- Therefore the public key of the signer is , and the private key is .
Anonymous Credential Light (ACL)
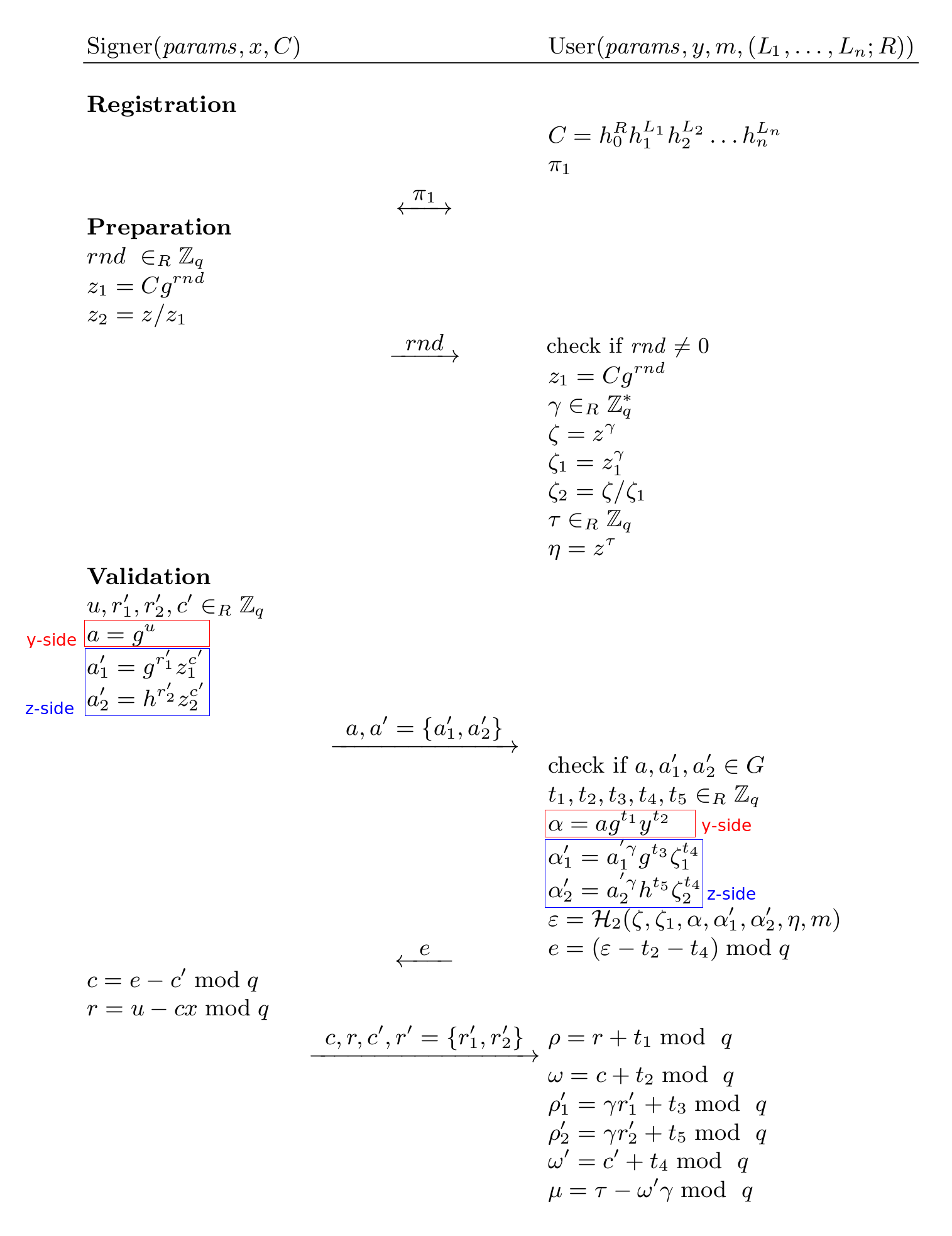
In a nutshell, the protocol proceeds as follows. The user and the signer take inputs as described in the below figure. The user commits () to certain attributes that he claims he has. Then the user proves in zero-knowledge that he knows an opening of the commitment .
Then, the signer computes some one-time tag keys depending on randomness and the commitment and sends the randomness to the user so that he can check and compute the same one-time tag key.
The user computes another commitment which is a blinded Pedersen commitment to the same attributes. (See in the below figure)
The signer and the user perform two protocols ( using the OR-proof technique). In the end, the user forms the blind signature with attributes that is an 8-tuple, i.e. , where encodes the attributes of the user. Note that corresponds to the commitment . (see the below figure)
Signature / Credential issuing
The signature issuing scheme is run in three phases, i.e. registration, preparation, and validation. The registration phase is a one-time phase that should be performed only once for each user. The preparation and validation phases may be performed simultaneously.
Single-Use Credentials
Single-use anonymous credentials avoid double use of the same credential. If a user uses anonymous credentials with the same attributes twice, the verifier can reveal the user’s identity.
First, the user computes another commitment for some random (recall the definition of the Combined commitment scheme). Note that is specific to the credential. Then user sends to the signer, and he also sends a zero-knowledge proof of the opening of . The user and the signer participate in a blind signature protocol with the combined commitment , i.e. commitment to the set of attributes .
To use this credential (with )
- the user sends to the verifier,
- the verifier sends a challenge to the user,
- the user reveals the equation ``double-spending equation” to the verifier,
- The user provides a zero-knowledge proof that this information was revealed correctly,
In case of double use of a credential, a verifier can simply compute (which is the user’s public key) from the double-spending equations.
Relevancy assessment
This paper proposes an anonymous credential scheme that depends on a blind signature with attributes. The underlying signature scheme is used for proving the knowledge of some secrets with some zero-knowledge techniques.
The solution uses a different security assumption from the known ones. This makes it suitable for lightweight devices compared to the solutions using bilinear pairings.
This solution may give us useful ideas about the construction of an anonymous credential with the property of double-use detection.
References
[1] Masayuki Abe. A secure three-move blind signature scheme for polynomially many signatures. In EUROCRYPT, pages 136{151, 2001. https://www.iacr.org/cryptodb/data/paper.php?pubkey=1981